Discover 9 CISO-proven tactics to stop credential-based ransomware before it starts.
What You’ll Learn in This Strategic Brief:
- Why credential compromise—not malware—is the real threat behind modern ransomware attacks
- How BlackCat and Cactus are bypassing traditional defenses using identity-based tactics
- The 9 proven actions CISOs can take to reduce ransomware risk in 2025
- What it takes to detect ransomware before encryption starts, using identity behavior signals
- How Privileged Access Management plays a critical role in stopping lateral movement and extortion
When MGM's slot machines went dark for days in September 2023, the casino giant learned a $100 million lesson in ransomware evolution. The BlackCat attack that crippled their operations started with something deceptively simple: a phone call to the help desk. An attacker, posing as an IT employee, convinced the staff to provide VPN credentials.
Within hours, those stolen credentials became the foundation for one of the most devastating ransomware attacks in recent history.
The Identity Factor in Modern Ransomware
Roughly 90% of ransomware attacks begin the same way: with a stolen credential. Recent cybersecurity research reveals a 71% year-over-year increase in cyberattacks using stolen or compromised credentials.
Recent campaigns like BlackCat (ALPHV) and the emerging Cactus ransomware have weaponized identity compromise to devastating effect.
BlackCat operators encrypt your files, steal your data, leak it publicly, and sometimes launch DDoS attacks for good measure. Meanwhile, Cactus has introduced new stealth techniques that make traditional defenses nearly useless.
Your perimeter defenses are only as strong as your weakest credential. When attackers can simply walk through the front door with legitimate login credentials, firewalls and intrusion detection systems become irrelevant.
The challenge for security leaders is stark: how do you defend against threats that evolve faster than your security strategy? BlackCat affiliates recruited experienced cybercriminals from dismantled groups like REvil and DarkSide. Cactus emerged in 2023 with encryption techniques that bypass traditional antivirus completely.
This analysis examines the tactics, techniques, and procedures behind these advanced campaigns and translates them into nine strategic actions that CISOs can implement to strengthen ransomware resilience in 2025.
Anatomy of an Advanced Threat
BlackCat (ALPHV): The Identity Predator
BlackCat burst onto the ransomware scene in late 2021 as a highly sophisticated Ransomware-as-a-Service platform. What makes BlackCat particularly dangerous isn't just its technical capabilities. Rather, it's how the group has mastered identity-based attacks.
The credential harvesting operation runs like clockwork. BlackCat affiliates purchase stolen credentials from underground markets, conduct targeted phishing campaigns, and deploy advanced social engineering tactics. They call help desks pretending to be employees, convincing IT teams to reset passwords or provide access. When they encounter multi-factor authentication, they don't give up. They use advanced phishing frameworks to steal session cookies and one-time authentication codes.
Once inside with basic user credentials, attackers quickly move to compromise administrative accounts. This privilege escalation phase is where the real damage begins.
The group's "big-game hunting" approach targets large organizations across sectors, employing double and triple extortion tactics.
First, they steal data and threaten to publish sensitive information on public leak sites. Then comes the encryption. The MGM breach started with a single compromised help desk interaction that led to VPN access credentials. From there, lateral movement through the network took mere hours.
BlackCat's success rate isn't due to advanced malware. It's their mastery of identity exploitation.
Cactus: The Invisible Threat
Cactus ransomware, first observed in April 2023, represents something different. While BlackCat focuses on identity compromise as an entry point, Cactus perfects the art of staying hidden once inside your network.
The technical innovation is remarkable in its simplicity. Cactus encrypts itself within ZIP archives, appearing as harmless files to antivirus engines. Initial access typically occurs through unpatched Fortinet VPN vulnerabilities, which is another identity-adjacent attack vector. Once inside, attackers install backdoors and steal service account credentials for long-term persistence.
Before encryption begins, Cactus systematically removes security software from infected systems. The malware knows that detection is its biggest threat, so it eliminates the eyes and ears of your security team first.
Cactus assumes your perimeter will eventually be breached and focuses on maintaining persistent access through compromised identities and disabled defenses. This assumption-based approach makes it particularly dangerous for organizations with traditional security architectures.
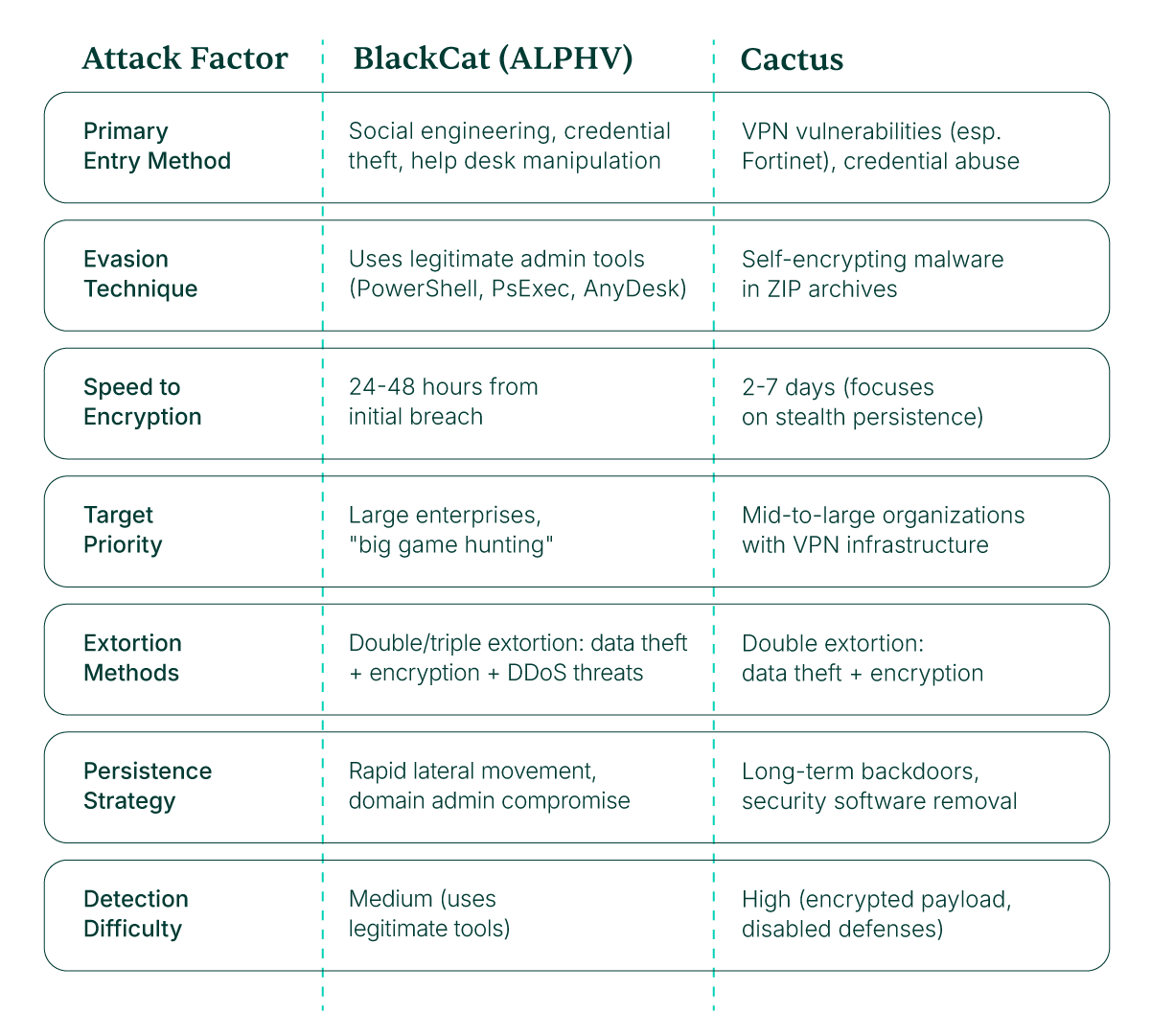
Threat Comparison: BlackCat vs. Cactus
Both ransomware groups exploit identity, but their methods and timelines differ dramatically.
Strategic Lessons for Prevention
Lesson 1: Treat Patch Management as Identity Protection
Both BlackCat and Cactus exploit known vulnerabilities as entry points, but the implications go deeper than simple system compromise. Cactus specifically targets unpatched Fortinet VPN gateways, while BlackCat affiliates have been observed chaining together 2-year-old CVEs in outdated systems like Backup Exec servers.
These aren't sophisticated zero-days. They're known flaws with available patches.
The Vulnerability-Identity Connection
Every unpatched vulnerability represents a potential pathway to credential theft. When attackers exploit a VPN server, they're positioning themselves to harvest user credentials and session tokens from active connections.
The lag time between patch release and widespread exploitation has shrunk dramatically. What used to be months is now weeks or days. Consider the risk-based approach differently: prioritize identity-adjacent systems in your patch management workflow.
Strategic Patch Prioritization
Create a tiered approach that treats identity infrastructure as critical:
- Tier 1 (48-72 hour patching): VPN gateways, authentication servers, privileged access management tools, and domain controllers
- Tier 2 (Weekly patching): Systems with service accounts or shared credentials, backup infrastructure, and remote access tools
- Tier 3 (Monthly cycle): Standard user workstations and isolated systems
Use threat intelligence feeds to identify which vulnerabilities ransomware groups are actively exploiting. Create "crown jewel" asset inventories that include all systems handling authentication and authorization.
What this means: Every delayed patch is an open invitation for credential compromise. Treat vulnerability management as the first line of identity defense.
Lesson 2: Assume Your Credentials Are Already Compromised
This lesson requires a fundamental shift in thinking.
BlackCat treats stolen credentials as its primary weapon, not its backup plan. They maintain databases of compromised accounts and actively purchase new credentials from underground markets. The MGM attack succeeded because attackers convinced help desk staff to provide VPN credentials and didn't need any technical exploitation.
Traditional approaches assume credentials are secure until proven otherwise. Modern ransomware flips this assumption: attackers assume they can compromise credentials and plan accordingly. Your security strategy should do the same.
Building Defense Through the Three P's Framework:
People: Social engineering remains the primary vector for credential compromise, making human awareness your first critical defense layer. Comprehensive security awareness training must specifically address ransomware tactics like vishing, pretexting, and help desk manipulation. Employees need to understand that they're often the first line of defense against credential theft.
Regular phishing simulations help reinforce these lessons while identifying areas for improvement, but the training must go beyond generic awareness to focus on the specific social engineering techniques that ransomware groups use to harvest credentials.
Processes: Awareness alone isn't sufficient when sophisticated attackers are involved. Your processes must assume that some social engineering attempts will succeed. This means implementing phishing-resistant multi-factor authentication across all systems, with hardware tokens and FIDO2 solutions that resist the advanced phishing frameworks bypassing SMS and app-based authentication.
Deploy robust Privileged Access Management with just-in-time access provisioning to eliminate standing administrative privileges and require approval workflows for elevated access. Establish clear verification procedures for help desk interactions and credential requests to prevent the social engineering tactics that enabled the MGM breach.
Products: Your security products must continuously monitor for the inevitable compromise attempts that slip through human and process defenses. Modern identity security platforms excel at detecting early signs of credential compromise through continuous risk assessment and behavioral analysis.
These solutions monitor for credential stuffing attempts, unusual login patterns, and privilege escalation indicators that traditional security tools often miss.
Even the most sophisticated technical controls won't help if users aren't educated about social engineering tactics and click on malicious links.
Some of your credentials are probably already compromised. Advanced identity threat detection can help you identify which ones before attackers leverage them for ransomware deployment.
Lesson 3: Secure Initial Access Vectors (Beyond the Perimeter)
Ransomware groups have abandoned the brute force approach. Instead, they walk through your front door with valid credentials. This requires rethinking how we approach access security.
BlackCat uses sophisticated phishing and voice-phishing campaigns to trick employees. Cactus exploits VPN appliances to gain initial network access. The attack surface has expanded beyond traditional network perimeters to include every point where identities intersect with systems.
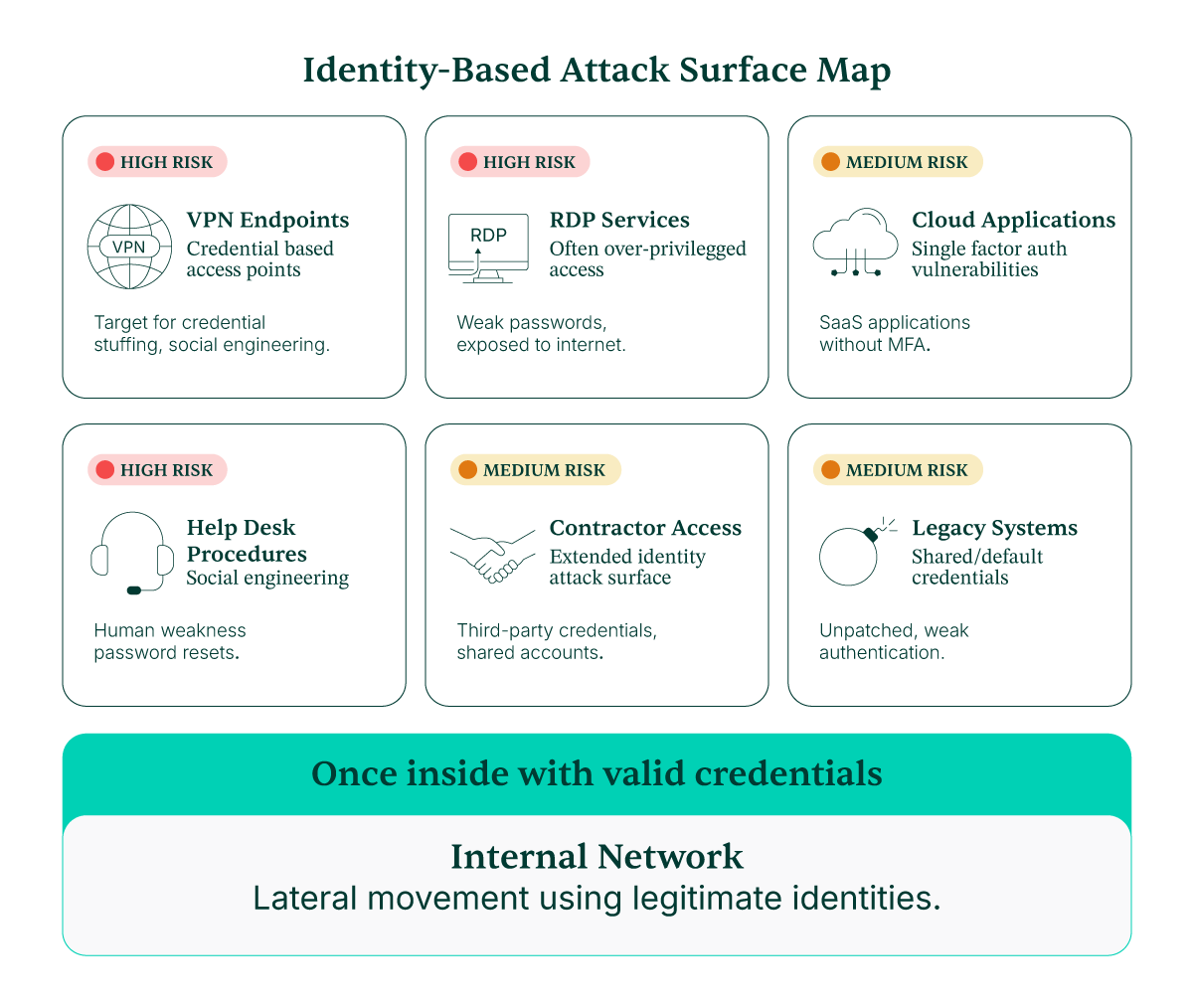
The expanding attack surface includes:
- VPN endpoints with weak authentication or unpatched vulnerabilities
- Remote Desktop Protocol services, often deployed for convenience without proper security controls
- Cloud applications with single-factor authentication, representing low-hanging fruit
- Help desk procedures, vulnerable to social engineering (as demonstrated in the MGM attack)
- Contractor and vendor access points that multiply the identity attack surface exponentially
- Legacy systems with shared accounts or default credentials
Audit all external-facing entry points and implement multi-factor authentication universally. Move beyond traditional VPNs to Zero Trust Network Access architectures that never trust, always verify. Strengthen help desk verification procedures with callback protocols and verbal verification codes.
Deploy advanced email security that detects sophisticated phishing attempts, including the kind of targeted campaigns that BlackCat affiliates use. Create vendor access policies that include identity verification requirements and regular access reviews.
Strategic Lessons for Detection
Lesson 4: Hunt for Identity Abuse, Not Just Malware
Traditional security approaches fail against modern ransomware because they're looking for the wrong indicators.
Why Traditional Detection Fails
Cactus hides its malicious code in encrypted archives that antivirus engines can't scan. BlackCat affiliates use legitimate administrative tools like PowerShell, PsExec, and AnyDesk to avoid detection. These attacks don't look malicious because they're using legitimate tools and processes. Signature-based security becomes nearly useless.
That's why the approach shifts from hunting for malware to hunting for unusual identity usage patterns.
Identity-Based Hunting Techniques
Focus detection efforts on these identity abuse patterns:
- Service accounts logging in from new locations or unusual times
- Administrative privileges used outside normal business hours or by accounts that rarely need elevation
- Bulk file access by accounts that typically handle limited data sets
- Legitimate tools performing unusual actions (7-Zip compressing thousands of files, PowerShell with suspicious parameters)
- Lateral movement indicators (PsExec connections to multiple systems, WMI commands in sequence)
- Security software tampering (attempts to disable EDR agents or delete security logs)
- Backup system access by non-administrative accounts or during unusual timeframes
Identity behavior analytics platforms use machine learning algorithms to establish baselines for normal user and entity behavior, then flag deviations that could indicate compromise.
These solutions go beyond traditional User and Entity Behavior Analytics by focusing specifically on identity usage patterns and privilege escalation attempts.
Modern PAM solutions have evolved to include sophisticated behavioral monitoring capabilities that can detect these patterns in real-time, often identifying credential abuse before traditional security tools recognize the threat.
Lesson 5: Connect the Identity Dots Across Your Environment
Ransomware attacks unfold across multiple systems and timeframes, often over days or weeks. A single compromised credential might be used to access email systems, then escalate to server access, then move laterally to backup infrastructure. Without correlation capabilities, these appear as separate, low-priority security events.
The Correlation Challenge
Most SOCs handle thousands of alerts daily. The early signs of credential compromise (failed login attempts, unusual access patterns, privilege escalation attempts) often get lost in alert fatigue or deprioritized due to volume.
Building Connected Detection
This is where identity-specific correlation capabilities become critical. While traditional SIEM solutions excel at correlating network and system events, identity security platforms provide deeper context about user behavior patterns and credential usage anomalies. These platforms can track identity risk across the complete attack chain—from initial credential compromise through privilege escalation to data exfiltration.
Enhance correlation engines to track identity-related events across all systems in your environment. Develop specific playbooks for investigating credential compromise scenarios. Implement Security Orchestration, Automation, and Response to automate initial triage and investigation steps.
Create dashboards that track identity risk indicators across the organization.
- Failed login attempts from unusual locations.
- Service account usage outside normal patterns.
- Administrative privilege usage by accounts that rarely need elevated access.
Establish clear escalation procedures for suspected identity compromise that involve both security and identity management teams.
The goal is to connect seemingly unrelated identity events into a coherent attack narrative before encryption begins.
Strategic Lessons for Response
Lesson 6: Practice Identity-Focused Incident Response
Some groups complete attacks from initial breach to full encryption in under 24 hours. When MGM was attacked, the speed of lateral movement through compromised identities meant containment windows measured in minutes, not hours.
Traditional incident response focuses on isolating infected systems. Identity-based attacks require isolating compromised accounts, which can be significantly more complex when those accounts have legitimate business purposes and active user sessions.
Update incident response playbooks to prioritize identity containment alongside system isolation. This means having pre-approved procedures for rapidly disabling suspicious accounts, even when you're not completely certain they're compromised.
Practice tabletop exercises that simulate credential compromise scenarios where normal business operations must continue while potentially compromised identities are investigated.
Create communication protocols for coordinating between security operations and identity management teams. Test your ability to quickly identify which systems a compromised account can access, which shared resources might be affected, and how to maintain business continuity while containing the threat.
The complexity multiplies when dealing with service accounts that support critical business processes. You need procedures for quickly rotating service account credentials without causing service outages.
Lesson 7: Segment Networks with Identity Context
Network segmentation without identity context is fundamentally flawed in the modern threat landscape.
Once BlackCat obtains domain administrator credentials, the malware can spread to virtually every system in a flat network architecture. The group uses tools like PsExec to push ransomware across entire environments almost simultaneously. Traditional network segmentation based on VLANs and subnets becomes irrelevant when attackers have legitimate credentials for multiple network zones.
The solution requires identity-aware network segmentation that considers user roles and access requirements.
Create network zones that isolate critical systems from general user access based on identity context, not just network topology. Deploy micro-segmentation around high-value assets like backup servers and domain controllers, with access controls that integrate directly with identity management systems.
Test segmentation effectiveness by simulating lateral movement scenarios using compromised credentials. Can a compromised user account from the marketing department access financial systems? Can a compromised service account jump between production and development environments?
Ensure network access controls integrate seamlessly with your identity management systems, so that identity changes automatically trigger network access adjustments.
Strategic Lessons for Recovery
Lesson 8: Protect Backups from Identity-Based Attacks
Both BlackCat and Cactus specifically target backup systems because they understand that reliable backups eliminate ransom payment pressure. BlackCat routinely deletes Windows shadow copies, while Cactus operators actively hunt for and compromise backup servers.
The Identity Backup Problem
Backup systems are often protected by the same domain credentials that attackers compromise during their initial network infiltration. If a ransomware group gains domain admin access, they likely have access to your backup infrastructure too.
This demands a rethinking of backup security architecture.
Isolation Architecture Requirements
Implement these backup security measures to protect against credential-based attacks:
- Immutable backup solutions that can't be modified even with administrative credentials
- Air-gapped backup systems with completely separate identity management (different Active Directory forests)
- Multi-person authorization for backup deletions and modifications
- Separate authentication systems for backup access (different administrative accounts)
- Regular restoration testing, assuming primary identity systems are compromised
- Backup access monitoring that alerts on unusual patterns or deletion attempts
Identity security solutions can help establish this isolation by creating completely separate identity domains for backup infrastructure, ensuring that the compromise of production credentials doesn't automatically grant access to backup systems.
Test backup restoration procedures regularly, but do so assuming your primary identity systems are compromised. Can you restore critical systems using only the air-gapped backup environment? How long does recovery take when you can't use your normal administrative accounts?
Many organizations discover backup compromises only after they need to restore from backups.
Lesson 9: Prepare for Identity-Driven Extortion
Modern ransomware extends far beyond file encryption. It's about leveraging stolen data for maximum pressure and long-term criminal profit.
BlackCat maintains public leak sites where they publish victim data, creating regulatory and reputational pressure that often exceeds the direct cost of business disruption. They also threaten DDoS attacks and direct contact with customers and partners. When ransomware groups steal data, they often prioritize identity-related information: employee credentials, customer authentication data, and privileged account information.
This data has ongoing value for future attacks and represents maximum embarrassment potential for victim organizations. Identity data breaches carry significant regulatory implications under frameworks like GDPR, CCPA, and sector-specific regulations.
Develop data breach response plans that specifically address identity data exposure scenarios. Implement data loss prevention solutions that monitor for credential and identity data exfiltration attempts. Create procedures for rapidly rotating potentially compromised credentials across all systems and applications.
Prepare customer and stakeholder communications for identity data breach scenarios. These communications are different from typical data breach notifications because they require advising affected individuals to change passwords and review account activity across multiple systems.
Consider cyber insurance policies that specifically cover identity-related data breaches and the unique costs associated with credential rotation and identity monitoring services.
The breach impact extends far beyond the immediate ransomware attack when identity data is involved. Plan for long-term identity security implications.
Building Your 2025 Identity-Centric Ransomware Resilience Roadmap
Integrating these lessons into your 2025 strategy requires a shift toward identity-centric security thinking.
Consider these strategic pillars for building comprehensive ransomware resilience:
Identity-First Threat Intelligence: Monitor threat feeds specifically for credential compromise indicators and identity-based attack techniques. Track which ransomware groups are targeting your industry's typical identity infrastructure. Understanding attacker psychology around identity compromise helps predict where they'll strike next.
Comprehensive Privileged Access Security Assessment: Regularly audit privileged accounts, assess credential hygiene, and test identity-based attack scenarios through red team exercises. You should evaluate their PAM implementations against the specific tactics used by groups like BlackCat and Cactus to identify gaps in privileged access controls. Finally, consider using specialized PAM tools like Segura to protect your privileged credentials
Identity-Aware Security Architecture: Design security tool integration around identity context. Ensure your SIEM, EDR, and network security solutions all understand user and entity behavior patterns. Identity should be the common thread connecting all security technologies.
Cross-Functional Identity Response: Break down silos between identity management, security operations, and incident response teams. Ransomware attacks exploit the gaps between these functions. Regular cross-team exercises help identify and close coordination gaps.
Identity Resilience Culture: Train employees to recognize that they protect organizational identities through their daily actions. Every password, every login, and every access request matters in the context of ransomware prevention.
Conclusion: Identity Security Is Ransomware Resilience
The sophisticated identity-based tactics demonstrated by BlackCat and Cactus represent the new reality for 2025: ransomware resilience starts with identity security.
These threats succeed not through advanced technical exploits, but by exploiting the fundamental trust relationships that make modern organizations function. When attackers can simply walk through the front door with legitimate credentials, traditional security architectures fail.
The nine lessons outlined provide a framework for building ransomware resilience that acknowledges this identity-centric threat landscape. Success requires moving beyond the traditional "castle and moat" security model to one that assumes identities will be compromised and plans accordingly.
The threat landscape will continue evolving, but by understanding how modern ransomware weaponizes identity compromise, you can build defenses that adapt to tomorrow's attacks while protecting against today's threats.
Strengthen Your Privileged Access Management Strategy
BlackCat and Cactus proved one thing: standing credentials are your riskiest asset. Segura® eliminates them before attackers can use them.
Implementing robust Privileged Access Management is no longer optional; it's essential for ransomware resilience. Segura®'s award-winning PAM platform directly addresses the identity security challenges highlighted throughout this analysis:
- Credential vaulting and rotation to eliminate the standing privileged credentials that BlackCat affiliates target
- Session monitoring and recording to detect unusual administrative activity that could indicate compromise
- Just-in-time access provisioning to minimize the window of opportunity for credential abuse
- Comprehensive audit trails for forensic analysis and compliance in the event of an incident
- Service account governance to secure the machine identities that ransomware often exploits for lateral movement
Our 360° Privilege Platform has earned the highest ratings from customers (4.9/5 on Gartner Peer Insights) and delivers 70% lower total cost of ownership with 7-minute deployment time.
Ready to strengthen your privileged access defenses against ransomware threats? Book a strategy call with our team to discuss how Segura® can help secure your most critical credentials and reduce your ransomware risk.
Frequently Asked Questions About Ransomware and Identity Security
What makes modern ransomware attacks like BlackCat and Cactus so hard to detect?
These groups use stolen credentials and legitimate admin tools (like PowerShell or PsExec) to move undetected. Because there’s often no obvious malware, traditional defenses miss the early warning signs.
How are credentials usually compromised in ransomware attacks?
Most incidents begin with phishing, social engineering, or abuse of unpatched identity systems like VPN gateways. In the MGM breach, attackers used a phone call to the help desk to gain VPN access.
Why isn’t MFA enough to stop ransomware anymore?
Advanced groups now bypass MFA using stolen session tokens or phishing kits that capture one-time codes. That’s why phishing-resistant authentication and least privilege controls are essential.
What role does PAM play in ransomware resilience?
Privileged Access Management limits what attackers can do with stolen credentials. Solutions like Segura help eliminate standing access, rotate credentials automatically, and monitor sessions in real time, closing the door before ransomware spreads.
How can I know if my team is vulnerable to identity-based ransomware?
Start by auditing all privileged accounts, service accounts, and access paths like VPNs, RDP, and legacy systems. Look for unused access, missing MFA, and overprovisioned roles. Segura’s platform includes tools for this type of discovery and risk reduction.